- September 22, 2022
- Posted by: admin
- Category: BitCoin, Blockchain, Cryptocurrency, Investments
The team at Sphinx is using the Validating Lightning Signer architecture to separate the keys from the Lightning node using a dedicated signing device.
The below is a direct excerpt of Marty’s Bent Issue #1264: “Don’t underestimate human creativity.” Sign up for the newsletter here.

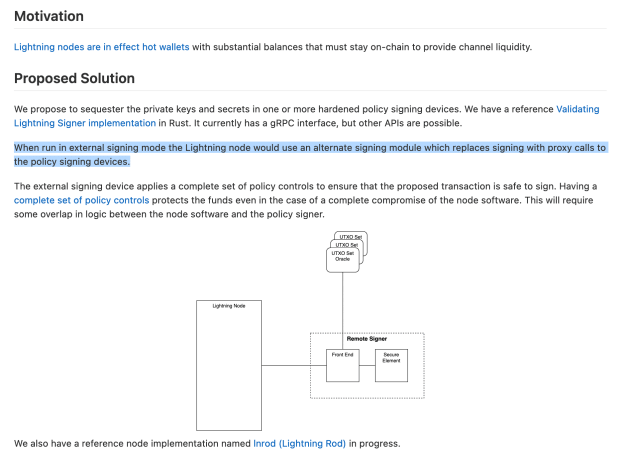
It’s true what they say: Bear markets are for building. Here’s a shining example of that via the Sphinx team showing that their Lightning node is leveraging the Validating Lightning Signer architecture, which separates the keys from the Lightning node using a dedicated signing device. That is what is pictured above: the small device hanging out of the wall outlet.
“Why the hell does this matter?” Very good question, freak. Up until this point (well really earlier this year when Nodl came out with their Nodlito project), running a Lightning Network node has been a very cumbersome process due to the need for 100% uptime to facilitate payments. This need for uptime has pushed many enterprise-level Lightning users to run their nodes in the cloud using server farms that can meet the uptime demands. This is a bit worrisome because it leads to these Lightning nodes being somewhat of sitting ducks. Since it has been common practice up to this point to house the node and the keys that grant users access to their Lightning channels in the same hardware, it would be trivial for a motivated attacker to identify and confiscate dedicated Lightning hardware sitting in server farms across the world, effectively allowing the attacker to confiscate a user’s bitcoin.
Enter schemes like Nodlito and Validating Lightning Signer, which bring a new way of doing things to the market. Instead of housing the keys and the node in the same hardware, thus creating a central point of failure, these projects aim to equip users with the means to separate the two functions and give those users back full control of their bitcoin by ensuring they can physically possess their keys using dedicated hardware that communicates with the node running in the cloud. Yes, the hardware running the node at a particular server farm can be shut off, but the user will still have their keys and, therefore, access to their bitcoin.
Here’s how the architecture for the Validating Lightning Signer looks:
If this type of Lightning node setup becomes commonplace, it could really open up the doors for more individuals to participate in building out the network without having to worry about running their own node hardware. Obviously, the most sovereign way to participate in the Lightning Network would be to run your own node, but the uptime demand to be a legitimate node operator prevents a significant amount of people from participating fully. It seems to me that this is a decent tradeoff to get more people running their node software in the cloud. Yes, those cloud providers are centralized entities. However, if you are able to hold your keys, you can operate with the peace of mind that you always have access to your money. And with more freedom-focused cloud providers like Nodl coming to market, the options available to Bitcoiners seem to be expanding.
Regardless, this type of architecture is very encouraging to see and it highlights something that I think many people who critique Bitcoin and many die-hard Bitcoiners overlook: The creativity of the people building on Bitcoin, Lightning and any other part of the stack will continue to surprise us. There is no one on the planet who can tell you what the stack will look like and exactly what it will provide in the future. This is why I often find it silly when people take a snapshot of the activity across the stack today and attempt to project out future activity on the network. We don’t know what we don’t know. And what we don’t know will continue to push the design landscape of what can and will be built on Bitcoin in the future. And that future seems to be very bright!
